 | |
| Network Secutity |
ComputerNetwork Security
One
of the most important automated tools for computer network security
is encryption. Encryption is a process that conceals meaning by
changing intelligible messages into unintelligible message.
Encryption can be by means of the following two systems:
code:
A code system uses a predefines table or dictionary to substitute
a meaningless word or phrase for each message or part of message.
Cipher:
A cipher used a computable algorithm that can translate any stream of
message bits into an unintelligible cryptogram.
Conventional
Encryption
The
original message, referred to as plaintext, is converted into
apparently random nonsense, referred to as ciphertext. The encryption
process of an algorithm and a key. The key is a relatively short bit
string that controls the algorithm. The algorithm will produce a
different output depending on the specific key being used at the
time. Changing the key radically changes the output of the algorithm.
Once
the ciphertext in produces, it is transmitted. Upon reception, the
ciphertext can be transformed back to the original plaintext by
using a decryption algorithm and the same key that was used for
encryption.
The
security of conventional encryption depends on the security of the
key, not the security of the algorithm secret; we only need to keep
the key secret. With the use of conventional encryption, the
principal security problem is maintaining the secrecy of the key.
Authentication
using conventional encryption:
It
is possible to perform authentication simply by the use of
conventional encryption. If we assume that only the sender and
receiver share a key, then only the genuine sender would be able to
successfully encrypt a message for the other participant.
Furthermore, if the message includes an error-detection code and a
sequence number, the receiver is assured that no alteration have been
made and that sequencing is proper. If the message also includes a
time stamp, the receiver is assured that the message has not been
delayed beyond that normally expected for network transit.
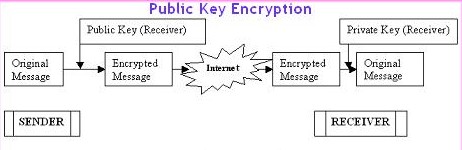
Public-key
encryption:
 |
| Public-key encryption |
In
public-key encryption, the algorithm uses one key for encryption and
a companion but different key for decryption. The technique works as
follows:
- Each end system in a network generates a pair of keys to be used for encryption and decryption of message that it will receive.
- Each system publishes its encryption key by placing it in a public register or file. This is the public key. The companion key is kept private.
- If sender wishes to send a message to receiver, it encrypts the message using receiver's public key.
- When receiver receives the message, it decrypts it using private key. No other recipient can decrypt since only receiver knows the private key.
Message
Authentication:
A
message, file, document or other collection of data is said to be
authentic when it is genuine and came from its alleged source.
Message authentication is a procedure that allows the communicating
parties to verify that received messages are authentic.
Message
Authentication Code:
One
authentication technique involves the use of a secret key to
generate a small block of data , known as message authentication
code, that is appended to the message. This technique assumes that
two communicating parties, say A and B, share a common secret key
KAB. When A has a message to send to B, it calculates the
message and the key: MACM = F(KAB, M). The
message plus code are transmitted to the intended recipient. The
recipient performs the same calculation on the receives message,
using the same secret key, to generate a new message authentication
code. The received code is compared to the calculated code. If we
assume that only the receiver and the sender know the identity of the
secret key, ans if the receives code matches the calculated code, then
- The receiver is assured that the message has not been altered.
- The receiver is assured that the message is form the alleged sender.
- If the message includes a sequence number, then the receiver can be assured of the proper sequence.
Related Post:

Computer and network security have become increasingly important issue across all industries or world. From protecting corporate networks from malware, hackers, and denial of service attacks to securing government networks from cyber espionage and cyber terrorism, modern network admin..
ReplyDelete_____________________
ultimate pet websites