Define
process, host and network with respect to TCP/IP protocol
architecture.
Ans:
The TCP/IP protocol suite is based on a view of communication that
involves three agents: process, host and networks. Processes are the
fundamental that communicate. A process executes on hosts, which can
often multiple simultaneous processes. Communication between
processes takes place across networks to which the hosts are
attached.
What is a gate way?
A gateway is processor connecting two networks whose primary function
is to relay data between networks using an internetworks protocol.
Name the general types of protocols seen to needed host-host layer.
Four general types of protocols seen to be needed host-host
protocol:-
- A reliable connection-oriented data protocol.
- A diagram protocol.
- A speech protocol
- A real-time data protocol
What is a subnetwork?
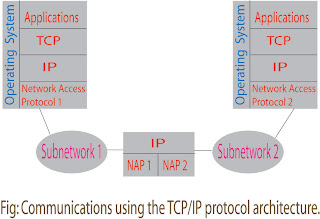
The TCP and IP protocols are configured for communications. The total
communications facility may consists of multiple networks, the
constituent networks are usually referred to as subnetworks.
What is a port?
For successful communication, every entity is the overall system must
have a unique address. Actually, Two levels of addressing are needed.
Each host on a subnetwork must have a unique global internet address;
this allows to be delivered to the proper host. Each process with a
host must have an address that is unique within the host; this allows
the host-to-host protocol (TCP) to deliver data to the proper
process. These latter addresses are known as ports.
Briefly describe the difference between the TCP/IP protocol suite and
OSI model.
There are fundamental differences between the TCP/IP protocol suit
and OSI model.
- Hierarchies versus layering: The OSI model is layered, but TCP/IP protocol suit is modular and hierarchical and gives the designer mode to develop efficient, cost-effective and rich protocol.
- Internetworking: Unlike the OSI model, the TCP/IP protocol suit places importance on internetworking between two different networks.
- Connectionless service: A connectionless service in one in which data are transferred from one entity to another without the prior mutual construction of a connection (e.g. datagram). The TCP/IP protocol suit places equal importance on connectionless and connection-oriented services, whereas the OSI model couched slowly in terms of connectionless service within the TCP/IP protocol suit is in internetworking.
- Management functions: the TCP/IP protocol suit and the OSI model differently treat the management-related functions.
Discuss the layers of the TCP/IP protocol architecture?
The protocol is organized into four layers:
- Network access layer
- Internet layer
- Host-to-host layer
- Process/application layer
a)
Network access layer: the network access layer contains those
protocols that provide access to a communication networks. Protocols
at this layer are between a communications node and an attached host.
A function of all these protocols id to route data between hosts
attached to the same network. Other services provided are flow
control and error control between hosts and various qualities of
service features such as priority and security. A network layer
entity is typically invoked by an entity is either the internet or
host-host layer but may be invoked by a process/application layer
entity.
b)
The internet layer: The internet layer consists of the procedures
required to allow data to traverse multiple networks between hosts.
Thus it must provide a routing function. This protocol is usually
implemented within hosts and gateways. A gateway is a processor
connecting two networks whose primary function is to relay data
between networks using a n internetwork protocol.
c)The
host-host layer: The host-host layer contains protocol entities with
the ability to deliver data between two processes on different host
computers. A protocol entity at this level may (or may not) provide a
logical connection between higher level entities. Other possible
services include error and flow control and the ability to deal with
control signals not associated with a logical data connection.
Four general types of protocols seen to be needed at this level:
- A reliable connection-oriented data protocol
- A datagram protocol
- A speech protocol
- A real time data protocol
- The process/application layer: The process and application layer contains protocols for resource sharing and remote access within the TCP/IP protocol suit architecture, there are the following protocol standards:
- Internet Protocol (IP): Which provides a connectionless service for and systems to communicate across one or more networks and does not assure the networks to be reliable.
- Host-host layer: Transmission control protocol (TCP), which provides a reliable end-to-end data transfer service.
- Process/application layer:
- File transfer protocol (FTP), which is a simple application for transfer of ASCII, EBCDIC and binary files.
- Simple mail transfer protocol (SMTP), which is simple electronic mail facility.
- Telnet protocol (TELNET): which provides a simple asynchronous terminal capability?
Discuss about the operation of TCP/IP protocols with suitable
diagram.
TCP and IP protocol are configured for communications. The total
communications facility may consists of multiple networks; the
constituent networks are usually referred to as subnetworks. Some
sort of network access protocol is used to connect a computer to a
subnetwork. This protocol enables the host to send data across the
subnetwork to another host or, in the case of a host on another
subnetwork, to a router. IP is implemented in all of the end systems
and routers. It acts as a relay to move a block of data from one
host, through one or a more routers, to another host. TCP is
implemented only in the end systems; it keeps track of the blocks of
data and assures that all are delivered reliably to the appropriate
application.
For
successful communication, every entity in the overall system must
have a unique address. Actually, two levels of addressing are needed.
Each host on a subnetwork has a unique global internet address; this
allows the data to be delivered to the proper host. Each process with
a host must have an address that is unique within the host; this
allows the host-to-host protocol (TCP) to deliver data to the proper
process. These latter addresses are known as ports.
Suppose
that a process, associated with port 1 at host A, wishes to send a
message to another process, associated with port 2 at host B. The
process at hands the message down to TCP with instructions to send it
to host B, port 2. TCP hands the message down to IP with instruction
to send it to host B. Next, IP hands the message down to the network
access layer with instructions to send it to router X
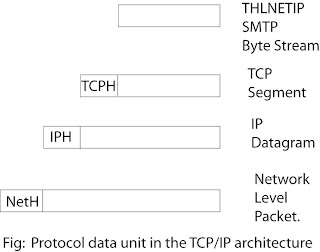
To
control this operation , control information as well user data must
be transmitted, as in figure(below). The sending process generates a
block into smaller pieces to make it more manageable. To each of
these pieces, TCP appends control information known as the TCP
header, forming a TCP segment. The control information is to be used
by the peer TCP protocol entity at host B. Examples of items that are
included in this header are Destination port, Sequence number and
checksum.
Next,
TCP hands each segment over to IP, with instruction to transmit it to
B. These segments must be transmitted across one or more subnetworks
and relayed through one or more intermediate routers. This operation
requires the use of control information. Thus IP appends a header of
control information to each segment to form an IP datagram. An
example of an item stored in the IP header is the destination host
address.
Each
IP datagram is presented to the network access layer for transmission
across the first subnetwork in its journey to the destination. The
network access layer appends its own header, creating a packet, or
frame. The packet is transmitted across the subnetwork to router X.
The pocket header contains the information that the subnetwork needs
to transfer the data across the subnetwork. Examples of items that
may be contained in this header include Destination subnetwork
address and Facilities requested.
At
router X, the packet header is stripped off and the PP header
examined. On the basis of the destination address information in the
IP header, the router directs the datagram out across subnetwork 2 to
B. To do this, the datagram is again augmented with a network access
header.
When
the data are received at B, the reverse process occurs. At each
layer, the corresponding header is removed, and the remainder is
passed on to the next higher layer until the original passed on to
the next higher layer until the original user data are delivered to
the destination process.

The TCP/IP Protocol Suite (also known as Transmission Control Protocol/Internet Protocol or TCP-IP). More complicated architectures, such as fully-resilient tiered structures are more suited to larger businesses and those with specific security or performance issues.
ReplyDelete_____________________
ultimate pet websites
Ararvitcurdo Sabrina Wallace https://wakelet.com/@tenpartdachar774
ReplyDeletenuymathandther